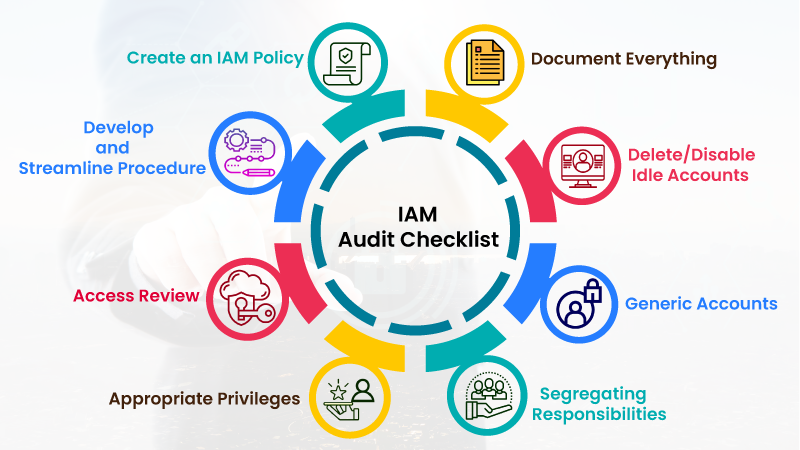
8 Key Steps For Effective Iam Audit And Iam Strategy
Find inspiration for 8 Key Steps For Effective Iam Audit And Iam Strategy with our image finder website, 8 Key Steps For Effective Iam Audit And Iam Strategy is one of the most popular images and photo galleries in 8 Best Practices For Robust Iam Strategy Gallery, 8 Key Steps For Effective Iam Audit And Iam Strategy Picture are available in collection of high-quality images and discover endless ideas for your living spaces, You will be able to watch high quality photo galleries 8 Key Steps For Effective Iam Audit And Iam Strategy.
aiartphotoz.com is free images/photos finder and fully automatic search engine, No Images files are hosted on our server, All links and images displayed on our site are automatically indexed by our crawlers, We only help to make it easier for visitors to find a free wallpaper, background Photos, Design Collection, Home Decor and Interior Design photos in some search engines. aiartphotoz.com is not responsible for third party website content. If this picture is your intelectual property (copyright infringement) or child pornography / immature images, please send email to aiophotoz[at]gmail.com for abuse. We will follow up your report/abuse within 24 hours.
Related Images of 8 Key Steps For Effective Iam Audit And Iam Strategy
8 Key Steps For Effective Iam Audit And Iam Strategy
8 Key Steps For Effective Iam Audit And Iam Strategy
800×450
Top 8 Best Practices To Accelerate Cloud Iam Adoption
Top 8 Best Practices To Accelerate Cloud Iam Adoption
700×1172
8 Key Steps For Effective Iam Audit And Iam Strategy
8 Key Steps For Effective Iam Audit And Iam Strategy
800×450
8 Key Steps For Effective Iam Audit And Iam Strategy
8 Key Steps For Effective Iam Audit And Iam Strategy
800×450
11 Identity And Access Management Iam Best Practices In 2023 Strongdm
11 Identity And Access Management Iam Best Practices In 2023 Strongdm
1560×876
How To Address Gdpr Phishing And Shadow It With A Robust Iam Strategy
How To Address Gdpr Phishing And Shadow It With A Robust Iam Strategy
2048×1152
Iam Best Practices Ensuring Robust Security In Aws Deployments By
Iam Best Practices Ensuring Robust Security In Aws Deployments By
800×453
Identity Access Management Iam The Vital Security Framework Dts
Identity Access Management Iam The Vital Security Framework Dts
1500×500
Best Practices For Effective Identity And Access Management Iam
Best Practices For Effective Identity And Access Management Iam
1000×525
10 Best Practices For Building A Robust Iam Strategy In 2024 The New
10 Best Practices For Building A Robust Iam Strategy In 2024 The New
1024×576
6 Iam Implementation Solutions For It Security Challenges
6 Iam Implementation Solutions For It Security Challenges
800×422
Identity Management Consulting Threat Protection Iam Vendor
Identity Management Consulting Threat Protection Iam Vendor
1500×1500
Top 5 Identity And Access Management Iam Best Practices
Top 5 Identity And Access Management Iam Best Practices
900×506
Top 8 Best Practices To Accelerate Cloud Iam Adoption
Top 8 Best Practices To Accelerate Cloud Iam Adoption
700×450
Iam Best Practices For Optimal Cloud Security Services
Iam Best Practices For Optimal Cloud Security Services
800×519
10 Best Practices For Building A Robust Iam Strategy In 2024 The New
10 Best Practices For Building A Robust Iam Strategy In 2024 The New
633×148
Iam Best Practices In Changing Environments Identity Management
Iam Best Practices In Changing Environments Identity Management
1030×579
10 Best Practices For Building A Robust Iam Strategy In 2024 The New
10 Best Practices For Building A Robust Iam Strategy In 2024 The New
889×539
Top 5 Identity And Access Management Iam Best Practices
Top 5 Identity And Access Management Iam Best Practices
900×506
10 Best Practices For Building A Robust Iam Strategy In 2024 The New
10 Best Practices For Building A Robust Iam Strategy In 2024 The New
665×391
Iam Best Practices For Enterprise Security Safeguarding Your Business
Iam Best Practices For Enterprise Security Safeguarding Your Business
1200×800
A Closer Look At Identity And Access Management Iam And Privileged
A Closer Look At Identity And Access Management Iam And Privileged
1000×1000
What Are The Best Identity And Access Management Iam Practices To
What Are The Best Identity And Access Management Iam Practices To
533×504
Iam Best Practices For The Most Favourable Cloud Security Ismile
Iam Best Practices For The Most Favourable Cloud Security Ismile
1024×576
An Introduction To Aws Iam Best Practices Techtarget
An Introduction To Aws Iam Best Practices Techtarget
520×468
