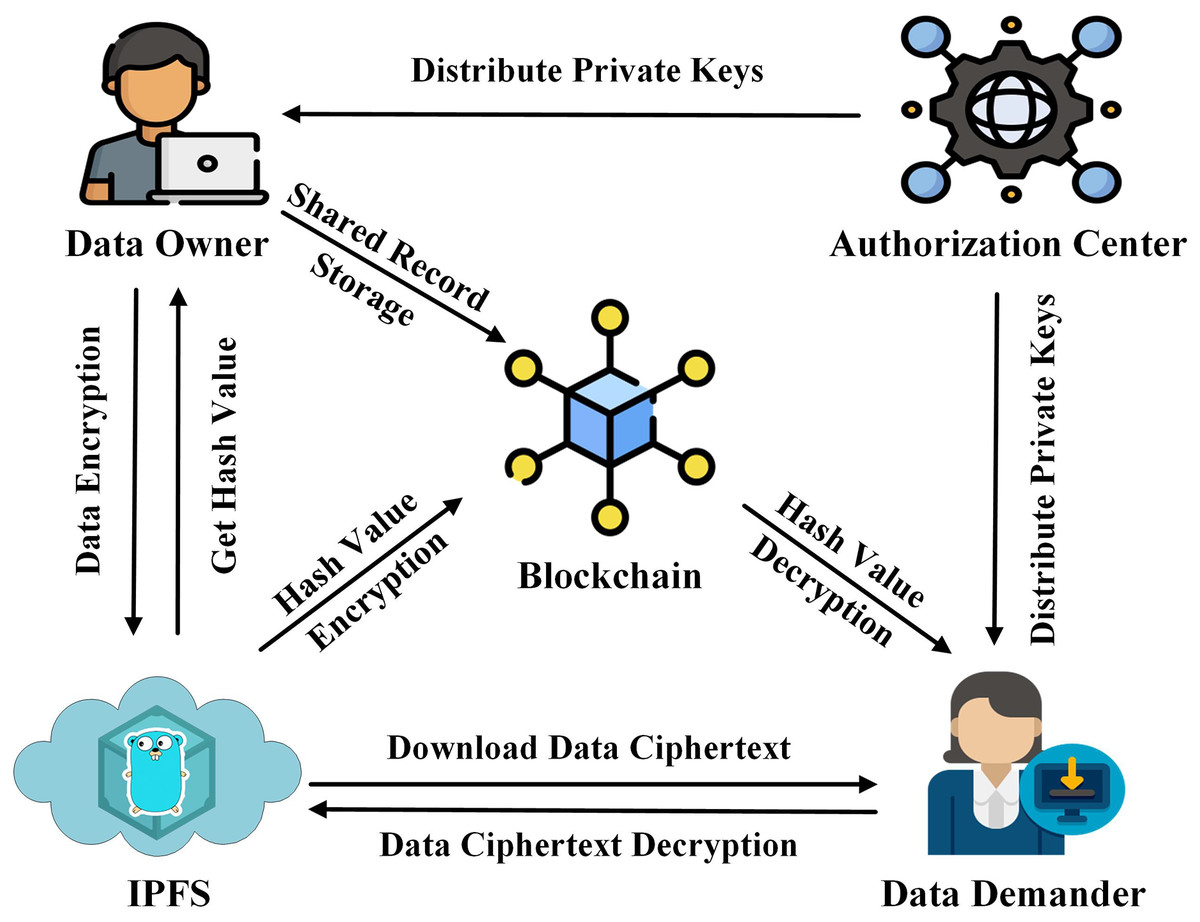
A Blockchain Based Traceable And Secure Data Sharing Scheme Peerj
Find inspiration for A Blockchain Based Traceable And Secure Data Sharing Scheme Peerj with our image finder website, A Blockchain Based Traceable And Secure Data Sharing Scheme Peerj is one of the most popular images and photo galleries in Secure Data Collectiopn Images Gallery, A Blockchain Based Traceable And Secure Data Sharing Scheme Peerj Picture are available in collection of high-quality images and discover endless ideas for your living spaces, You will be able to watch high quality photo galleries A Blockchain Based Traceable And Secure Data Sharing Scheme Peerj.
aiartphotoz.com is free images/photos finder and fully automatic search engine, No Images files are hosted on our server, All links and images displayed on our site are automatically indexed by our crawlers, We only help to make it easier for visitors to find a free wallpaper, background Photos, Design Collection, Home Decor and Interior Design photos in some search engines. aiartphotoz.com is not responsible for third party website content. If this picture is your intelectual property (copyright infringement) or child pornography / immature images, please send email to aiophotoz[at]gmail.com for abuse. We will follow up your report/abuse within 24 hours.
Related Images of A Blockchain Based Traceable And Secure Data Sharing Scheme Peerj
Secure Data Folder Icon From Cyber Security Collection Simple Line
Secure Data Folder Icon From Cyber Security Collection Simple Line
800×800
Secure File Sharing And Content Collaboration With Encryption
Secure File Sharing And Content Collaboration With Encryption
1272×974
Keep Your Sensitive Data Secure In 2020 With These 5 Steps
Keep Your Sensitive Data Secure In 2020 With These 5 Steps
1200×1200
Secure Data Collection Storage And Access In Cloud Assisted Iot
Secure Data Collection Storage And Access In Cloud Assisted Iot
1086×758
Blockchain Security Everything You Need To Know
Blockchain Security Everything You Need To Know
1600×700
Taking Control Of Your Data Security With Microsoft Steeves And
Taking Control Of Your Data Security With Microsoft Steeves And
3263×2238
Unlock Best Practices For Responsible Data Collection Today
Unlock Best Practices For Responsible Data Collection Today
1024×585
Data Governance With File And Information Processing Outline Collection
Data Governance With File And Information Processing Outline Collection
1600×1370
Electronics Free Full Text Enhanced Cloud Storage Encryption
Electronics Free Full Text Enhanced Cloud Storage Encryption
2219×1665
4 Ways Your Business Can Ensure Secure Data Privacy Heat Herdaniel
4 Ways Your Business Can Ensure Secure Data Privacy Heat Herdaniel
1200×800
Encrypted Forms Secure Data Collection With Zoho Forms
Encrypted Forms Secure Data Collection With Zoho Forms
1016×710
Planetverify — The Fastest And Safest Way To Collect Applicant Data
Planetverify — The Fastest And Safest Way To Collect Applicant Data
545×497
A Blockchain Based Traceable And Secure Data Sharing Scheme Peerj
A Blockchain Based Traceable And Secure Data Sharing Scheme Peerj
1200×922
How To Determine What Data Privacy Security Controls Your Business
How To Determine What Data Privacy Security Controls Your Business
2048×1365
What Is Database Security Standards Threats Protection
What Is Database Security Standards Threats Protection
1480×1050
5 Essential Data Security Best Practices For Keeping Your Data Safe
5 Essential Data Security Best Practices For Keeping Your Data Safe
1645×1057
5 Online Data Collection Methods To Improve Your Business Intelligence
5 Online Data Collection Methods To Improve Your Business Intelligence
1773×1182
Data Security And Confidentiality Acs Data Recovery
Data Security And Confidentiality Acs Data Recovery
775×300
Ipswitch Shares Insights For Ensuring Secure File Transfer
Ipswitch Shares Insights For Ensuring Secure File Transfer
865×432
Fully Leveraging Digital Loan Processing Efficiency Starts With
Fully Leveraging Digital Loan Processing Efficiency Starts With
600×400
Ppt Rapidly Developing A Secure Data Collection Environment
Ppt Rapidly Developing A Secure Data Collection Environment
720×540
How To Ensure Video Chain Of Evidence Kintronics
How To Ensure Video Chain Of Evidence Kintronics
600×600
Direct Mail Data Security Ensuring Privacy And Customer Confidence I
Direct Mail Data Security Ensuring Privacy And Customer Confidence I
1600×962
Pdf Secure Data Collection And Transmission For Iomt Architecture
Pdf Secure Data Collection And Transmission For Iomt Architecture
850×1173
Webinar Building A Portal For Secure Data Collection And Reporting
Webinar Building A Portal For Secure Data Collection And Reporting
1344×768
Unlock Best Practices For Responsible Data Collection Today
Unlock Best Practices For Responsible Data Collection Today
870×272
5 Tips For Secure Customer Data Collection Elasticit
5 Tips For Secure Customer Data Collection Elasticit
1024×585
Data Security And Compliance Oriental Solutions
Data Security And Compliance Oriental Solutions
800×350
Secure Data Data Storage Solution Secure Your Data
Secure Data Data Storage Solution Secure Your Data
1068×802
Data Storage Options For Cloud Storage And Internal Storage And The
Data Storage Options For Cloud Storage And Internal Storage And The
1600×1690
Database Secure Connection Icon From Technology Outline Collection
Database Secure Connection Icon From Technology Outline Collection
640×640
Secure Data Collection Process Cardiovascular Health And Needs
Secure Data Collection Process Cardiovascular Health And Needs
