Authentication Protocols Types And Uses Adaptive
Find inspiration for Authentication Protocols Types And Uses Adaptive with our image finder website, Authentication Protocols Types And Uses Adaptive is one of the most popular images and photo galleries in Authentication Protocols Types And Uses Adaptive Gallery, Authentication Protocols Types And Uses Adaptive Picture are available in collection of high-quality images and discover endless ideas for your living spaces, You will be able to watch high quality photo galleries Authentication Protocols Types And Uses Adaptive.
aiartphotoz.com is free images/photos finder and fully automatic search engine, No Images files are hosted on our server, All links and images displayed on our site are automatically indexed by our crawlers, We only help to make it easier for visitors to find a free wallpaper, background Photos, Design Collection, Home Decor and Interior Design photos in some search engines. aiartphotoz.com is not responsible for third party website content. If this picture is your intelectual property (copyright infringement) or child pornography / immature images, please send email to aiophotoz[at]gmail.com for abuse. We will follow up your report/abuse within 24 hours.
Related Images of Authentication Protocols Types And Uses Adaptive
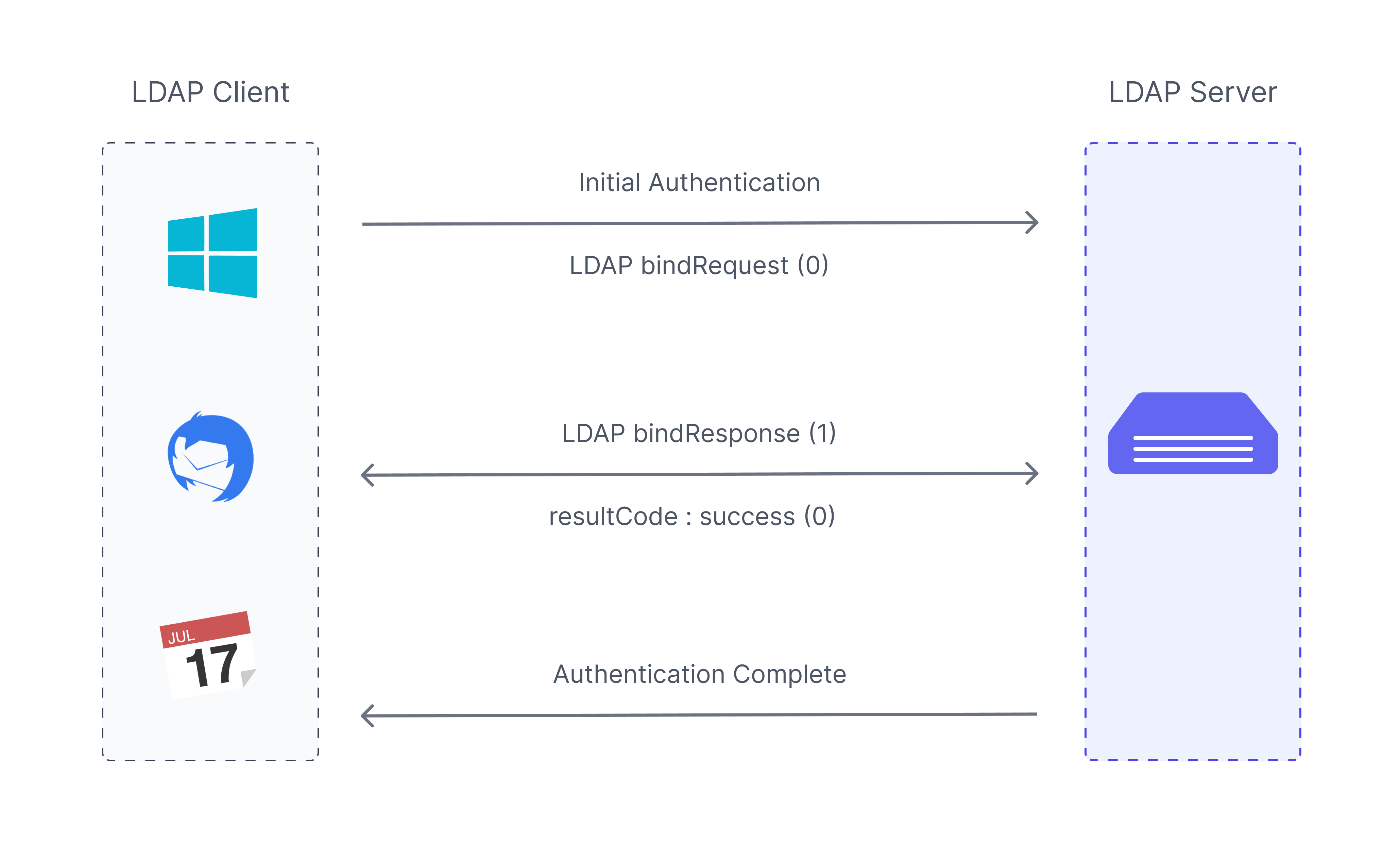
Authentication Protocols Types And Uses Adaptive
Authentication Protocols Types And Uses Adaptive
4118×2482
Authentication Protocols Types And Uses Adaptive
Authentication Protocols Types And Uses Adaptive
4118×2482
Authentication Protocols Types And Uses Adaptive
Authentication Protocols Types And Uses Adaptive
1800×945
Adaptive Authentication Protocols Types And Uses
Adaptive Authentication Protocols Types And Uses
1920×1008
Authentication Protocols Types And Uses Adaptive
Authentication Protocols Types And Uses Adaptive
4118×2482
Authentication Protocols Types And Uses Adaptive
Authentication Protocols Types And Uses Adaptive
4118×2482
Types Of Authentication Protocols Geeksforgeeks
Types Of Authentication Protocols Geeksforgeeks
1341×1228
Adaptive Authentication For Modern Identity Management Identity
Adaptive Authentication For Modern Identity Management Identity
800×400
Types Of Authentication Protocols Geeksforgeeks
Types Of Authentication Protocols Geeksforgeeks
1317×1241
Types Of Authentication Protocols Geeksforgeeks
Types Of Authentication Protocols Geeksforgeeks
1324×1223
Email Authentication Protocols What Are They And Why Are They Important
Email Authentication Protocols What Are They And Why Are They Important
1600×900
Ppt Authentication Protocols Powerpoint Presentation Free Download
Ppt Authentication Protocols Powerpoint Presentation Free Download
1024×768
Types Of Authentication Protocols Geeksforgeeks
Types Of Authentication Protocols Geeksforgeeks
1324×1245
Types Of Authentication Protocols Download Scientific Diagram
Types Of Authentication Protocols Download Scientific Diagram
850×465
Layer Up Your Account Security With Multi Factor Authentication Mfa
Layer Up Your Account Security With Multi Factor Authentication Mfa
2560×2560
Network Authentication Protocols Types And Their Pros And Cons Auvik
Network Authentication Protocols Types And Their Pros And Cons Auvik
967×733
Types Of Authentication Protocols Geeksforgeeks
Types Of Authentication Protocols Geeksforgeeks
1324×1241
Comparison Of Authentication Protocols Download Table
Comparison Of Authentication Protocols Download Table
640×640
Authentication Protocols 8021x Eappeap Eap Fasttlsttls And
Authentication Protocols 8021x Eappeap Eap Fasttlsttls And
1920×1080
What Is Token Based Authentication Types Pros And Cons
What Is Token Based Authentication Types Pros And Cons
800×388
What Is Extensible Authentication Protocol Eap And How Does It Work
What Is Extensible Authentication Protocol Eap And How Does It Work
992×558
What Is The Extensible Authentication Protocol Eap
What Is The Extensible Authentication Protocol Eap
560×314
Extensible Authentication Protocol Eap By Wentz Wu Issap Issep
Extensible Authentication Protocol Eap By Wentz Wu Issap Issep
1280×720
8021x Extensible Authentication Protocol Flexible Authentication Via
8021x Extensible Authentication Protocol Flexible Authentication Via
502×577
The Iot Authentication Process Download Scientific Diagram
The Iot Authentication Process Download Scientific Diagram
850×792
Email Authentication Protocols Spf Dkim Dmarc And Bimi Explained
Email Authentication Protocols Spf Dkim Dmarc And Bimi Explained
720×450
Ppt Network Plus Security Review Powerpoint Presentation Free
Ppt Network Plus Security Review Powerpoint Presentation Free
1024×768
How To Use Iot Authentication And Authorization For Security Techtarget
How To Use Iot Authentication And Authorization For Security Techtarget
560×297
