Creating A Vulnerability Management Strategy Zsecurity
Find inspiration for Creating A Vulnerability Management Strategy Zsecurity with our image finder website, Creating A Vulnerability Management Strategy Zsecurity is one of the most popular images and photo galleries in Creating A Vulnerability Management Strategy Zsecurity Gallery, Creating A Vulnerability Management Strategy Zsecurity Picture are available in collection of high-quality images and discover endless ideas for your living spaces, You will be able to watch high quality photo galleries Creating A Vulnerability Management Strategy Zsecurity.
aiartphotoz.com is free images/photos finder and fully automatic search engine, No Images files are hosted on our server, All links and images displayed on our site are automatically indexed by our crawlers, We only help to make it easier for visitors to find a free wallpaper, background Photos, Design Collection, Home Decor and Interior Design photos in some search engines. aiartphotoz.com is not responsible for third party website content. If this picture is your intelectual property (copyright infringement) or child pornography / immature images, please send email to aiophotoz[at]gmail.com for abuse. We will follow up your report/abuse within 24 hours.
Related Images of Creating A Vulnerability Management Strategy Zsecurity
Creating A Vulnerability Management Strategy Zsecurity
Creating A Vulnerability Management Strategy Zsecurity
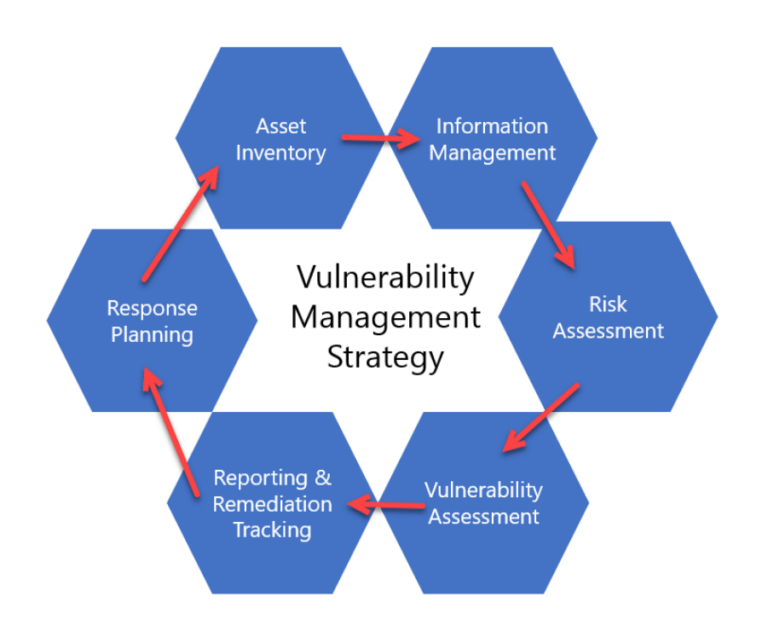
768×620
Creating A Vulnerability Management Strategy Zsecurity
Creating A Vulnerability Management Strategy Zsecurity
768×357
Vulnerability Management Strategies Types And Tools
Vulnerability Management Strategies Types And Tools
1231×745
Vulnerability Management Strategy Kratikal Blogs
Vulnerability Management Strategy Kratikal Blogs
1536×933
Vulnerability Managment Framework Application Security Code To Cloud
Vulnerability Managment Framework Application Security Code To Cloud
1091×690
Steps To Creating A Robust Vulnerability Management Process In 2023
Steps To Creating A Robust Vulnerability Management Process In 2023
1200×628
Steps To Create A Security Vulnerability Management Strategy
Steps To Create A Security Vulnerability Management Strategy
768×513
Vulnerability Management Ensl Group Ai Driven Cyber Security
Vulnerability Management Ensl Group Ai Driven Cyber Security
495×512
Vulnerability Management Strategies Types And Tools
Vulnerability Management Strategies Types And Tools
1200×675
8 Tips To Master Your Vulnerability Management Program Security Boulevard
8 Tips To Master Your Vulnerability Management Program Security Boulevard
748×463
Vulnerability Management An Essential Component Of Your Security Strategy
Vulnerability Management An Essential Component Of Your Security Strategy
720×720
How Vulnerability Management System Protects Businesses Outsource
How Vulnerability Management System Protects Businesses Outsource
1080×1080
Creating A Vulnerability Management Strategy Blog
Creating A Vulnerability Management Strategy Blog
1024×512
Vulnerability Management Vs Attack Surface Management Scrut Automation
Vulnerability Management Vs Attack Surface Management Scrut Automation
1024×894
The Vulnerability Management Lifecycle 5 Steps Crowdstrike
The Vulnerability Management Lifecycle 5 Steps Crowdstrike
2048×1102
Top 11 Best Practices For Efficient And Effective Vulnerability
Top 11 Best Practices For Efficient And Effective Vulnerability
1200×682
Cybersecurity And Vulnerability Management Strategy Watch Before Your
Cybersecurity And Vulnerability Management Strategy Watch Before Your
1200×628
Best Practices And Effective Vulnerability Management Strategy Set
Best Practices And Effective Vulnerability Management Strategy Set
550×678
Vulnerability Management Strategy Ebook Benjamin Allen
Vulnerability Management Strategy Ebook Benjamin Allen
902×480
Creating An Effective Enterprise Vulnerability Management Strategy
Creating An Effective Enterprise Vulnerability Management Strategy
998×1300
Need To Evolve To A Risk Based Vulnerability Management Strategy But
Need To Evolve To A Risk Based Vulnerability Management Strategy But
715×786
8 Steps To Build An Effective Vulnerability Management Program
8 Steps To Build An Effective Vulnerability Management Program
923×440
What Is Vulnerability Management Process And Best Practices Balbix
What Is Vulnerability Management Process And Best Practices Balbix
960×640
Top 5 Best Vulnerability Management Software For 2022 The
Top 5 Best Vulnerability Management Software For 2022 The
700×389
What You Need To Know To Improve Your Enterprise Vulnerability Mana
What You Need To Know To Improve Your Enterprise Vulnerability Mana
768×411
Vulnerability Management Strategy Everything You Need To Know Cymune
Vulnerability Management Strategy Everything You Need To Know Cymune
1920×1080
How To Build An Effective Vulnerability Management Program
How To Build An Effective Vulnerability Management Program
617×351
Threat And Vulnerability Management Xdr Platform Tips
Threat And Vulnerability Management Xdr Platform Tips
800×673
Vulnerability Management Lifecycle A Guide For 2024 — Informer
Vulnerability Management Lifecycle A Guide For 2024 — Informer
1440×850
What Is A Vulnerability Assessment Panda Security
What Is A Vulnerability Assessment Panda Security
1811×2560
Integrated Vulnerability And Patch Management Your First Step Towards
Integrated Vulnerability And Patch Management Your First Step Towards
