Cryptography Hash Function Coding Ninjas Codestudio
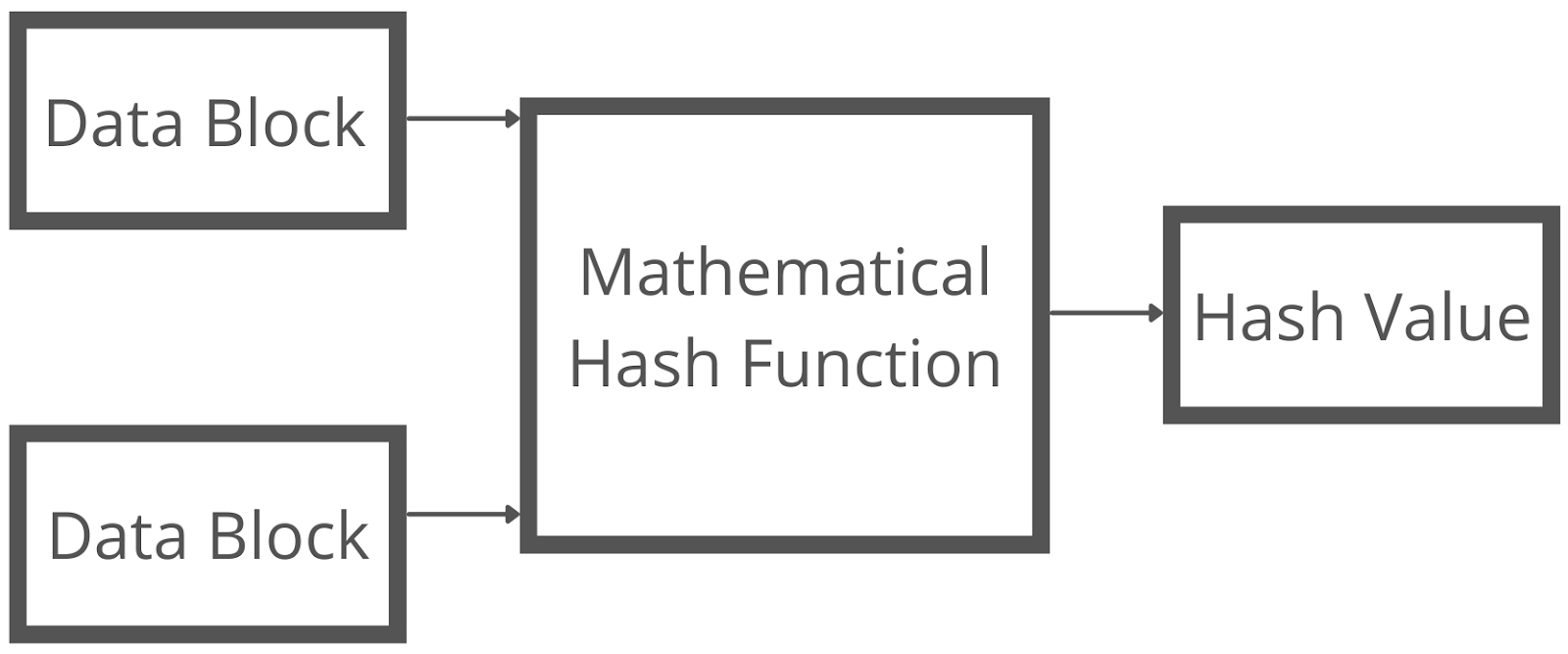
Find inspiration for Cryptography Hash Function Coding Ninjas Codestudio with our image finder website, Cryptography Hash Function Coding Ninjas Codestudio is one of the most popular images and photo galleries in Cryptography Hash Function Coding Ninjas Codestudio Gallery, Cryptography Hash Function Coding Ninjas Codestudio Picture are available in collection of high-quality images and discover endless ideas for your living spaces, You will be able to watch high quality photo galleries Cryptography Hash Function Coding Ninjas Codestudio.
aiartphotoz.com is free images/photos finder and fully automatic search engine, No Images files are hosted on our server, All links and images displayed on our site are automatically indexed by our crawlers, We only help to make it easier for visitors to find a free wallpaper, background Photos, Design Collection, Home Decor and Interior Design photos in some search engines. aiartphotoz.com is not responsible for third party website content. If this picture is your intelectual property (copyright infringement) or child pornography / immature images, please send email to aiophotoz[at]gmail.com for abuse. We will follow up your report/abuse within 24 hours.
Related Images of Cryptography Hash Function Coding Ninjas Codestudio
Cryptography Hash Function Coding Ninjas Codestudio
Cryptography Hash Function Coding Ninjas Codestudio
1600×667
Cryptography Hash Function Coding Ninjas Codestudio
Cryptography Hash Function Coding Ninjas Codestudio
1600×401
Full Domain Hash In Cryptography Coding Ninjas
Full Domain Hash In Cryptography Coding Ninjas
1200×700
Hash Functions And Data Integrity In Cryptography Coding Ninjas
Hash Functions And Data Integrity In Cryptography Coding Ninjas
1200×700
Security Of Hash Functions In Cryptography Coding Ninjas
Security Of Hash Functions In Cryptography Coding Ninjas
1200×700
Authenticated Encryption In Cryptography Coding Ninjas Codestudio
Authenticated Encryption In Cryptography Coding Ninjas Codestudio
1200×700
Security Of Hash Functions In Cryptography Coding Ninjas
Security Of Hash Functions In Cryptography Coding Ninjas
1200×700
Hash Functions And Data Integrity In Cryptography Coding Ninjas
Hash Functions And Data Integrity In Cryptography Coding Ninjas
1200×700
What Is Identity Based Cryptography Coding Ninjas Codestudio
What Is Identity Based Cryptography Coding Ninjas Codestudio
1600×900
The Merkle Damgard Construction In Hash Functions Coding Ninjas
The Merkle Damgard Construction In Hash Functions Coding Ninjas
1200×700
Hash Functions And Data Integrity In Cryptography Coding Ninjas
Hash Functions And Data Integrity In Cryptography Coding Ninjas
1200×700
What Are Key Updating In Cryptography Coding Ninjas
What Are Key Updating In Cryptography Coding Ninjas
1600×900
Security Of Hash Functions In Cryptography Coding Ninjas
Security Of Hash Functions In Cryptography Coding Ninjas
1200×700
Hash Functions And Data Integrity In Cryptography Coding Ninjas
Hash Functions And Data Integrity In Cryptography Coding Ninjas
1200×700
Code Based Cryptography Mceliece Cryptosystem Coding Ninjas
Code Based Cryptography Mceliece Cryptosystem Coding Ninjas
1200×700
Identity Based Cryptography Cryptography Coding Ninjas
Identity Based Cryptography Cryptography Coding Ninjas
1099×616
What Are Basic Cryptography Tools Coding Ninjas
What Are Basic Cryptography Tools Coding Ninjas
1024×572
Hash Functions And Data Integrity In Cryptography Naukri Code 360
Hash Functions And Data Integrity In Cryptography Naukri Code 360
1200×700
What Is A Hash Function In Cryptography A Comprehensive Study
What Is A Hash Function In Cryptography A Comprehensive Study
768×497
What Are Basic Cryptography Tools Coding Ninjas
What Are Basic Cryptography Tools Coding Ninjas
1366×768
Hash Functions And Data Integrity In Cryptography Naukri Code 360
Hash Functions And Data Integrity In Cryptography Naukri Code 360
819×286
Hash Functions And Data Integrity In Cryptography Naukri Code 360
Hash Functions And Data Integrity In Cryptography Naukri Code 360
660×225
Hash Function In Cryptography How Does It Work Infosec Insights
Hash Function In Cryptography How Does It Work Infosec Insights
1034×444
What Are Basic Cryptography Tools Coding Ninjas
What Are Basic Cryptography Tools Coding Ninjas
1366×768
What Is A Hash Function In Cryptography A Beginners Guide Hashed
What Is A Hash Function In Cryptography A Beginners Guide Hashed
1024×640
Cryptography And Network Security Coding Ninjas
Cryptography And Network Security Coding Ninjas
1150×680
