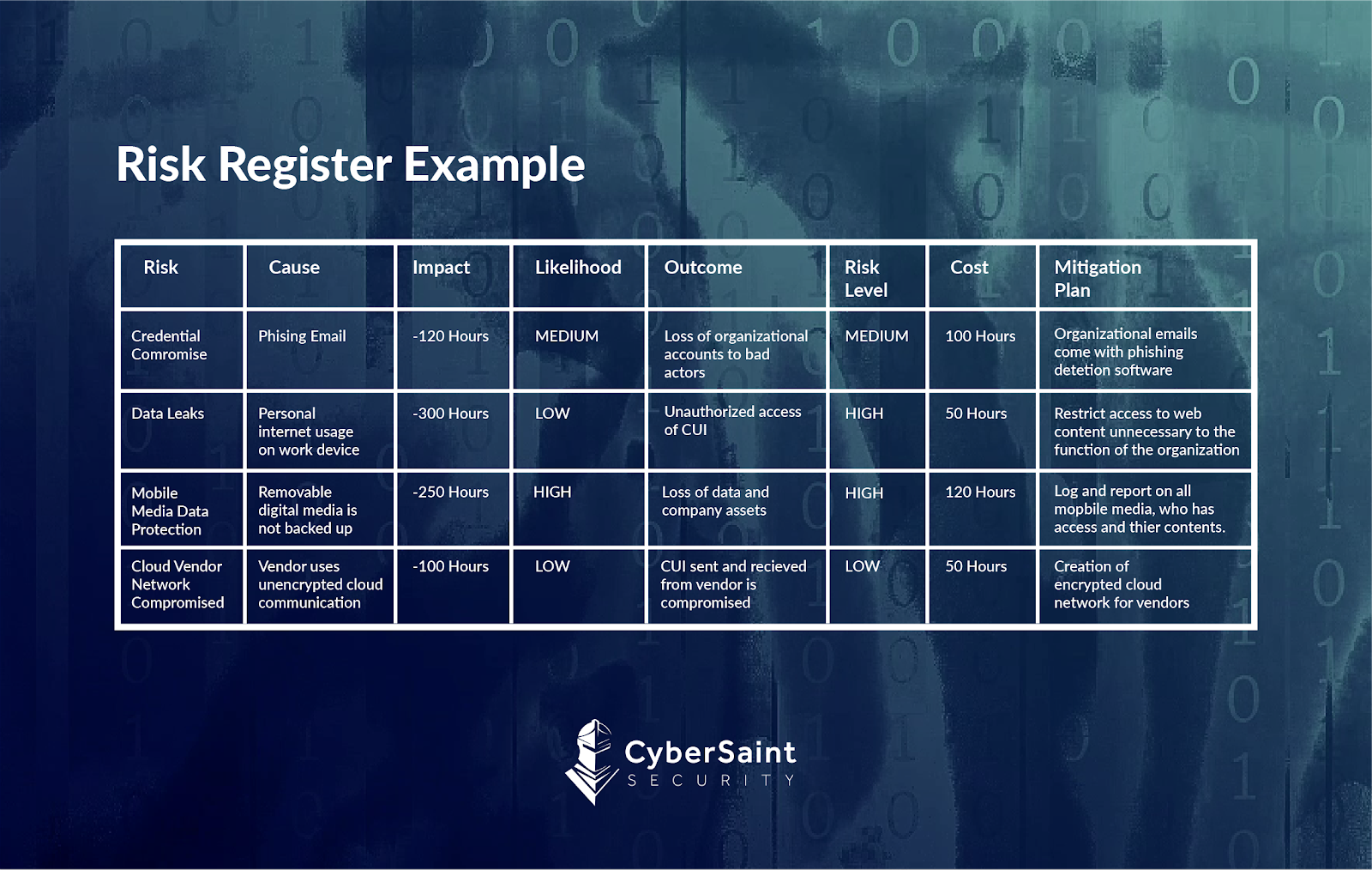
Cybersecurity Risk Register Template
Find inspiration for Cybersecurity Risk Register Template with our image finder website, Cybersecurity Risk Register Template is one of the most popular images and photo galleries in Html Attachments Are More Of A Security Risk Than Ever Heres What Gallery, Cybersecurity Risk Register Template Picture are available in collection of high-quality images and discover endless ideas for your living spaces, You will be able to watch high quality photo galleries Cybersecurity Risk Register Template.
aiartphotoz.com is free images/photos finder and fully automatic search engine, No Images files are hosted on our server, All links and images displayed on our site are automatically indexed by our crawlers, We only help to make it easier for visitors to find a free wallpaper, background Photos, Design Collection, Home Decor and Interior Design photos in some search engines. aiartphotoz.com is not responsible for third party website content. If this picture is your intelectual property (copyright infringement) or child pornography / immature images, please send email to aiophotoz[at]gmail.com for abuse. We will follow up your report/abuse within 24 hours.
Related Images of Cybersecurity Risk Register Template
Rh Isac Top 10 Web Application Security Risks
Rh Isac Top 10 Web Application Security Risks
1024×1024
How Html Attachments And Phishing Are Used In Bec Trend Micro Us
How Html Attachments And Phishing Are Used In Bec Trend Micro Us
641×350
Social Media Threats Attacks And Security Video And Lesson Transcript
Social Media Threats Attacks And Security Video And Lesson Transcript
1024×576
What Is Website Security How To Secure Your Website
What Is Website Security How To Secure Your Website
751×351
How Html Attachments And Phishing Are Used In Bec Trend Micro Us
How Html Attachments And Phishing Are Used In Bec Trend Micro Us
540×537
Protecting Your Site From The Most Critical Security Risks
Protecting Your Site From The Most Critical Security Risks
1200×582
The Top 10 Most Critical Application Security Risks Wp Engine Blog
The Top 10 Most Critical Application Security Risks Wp Engine Blog
824×342
Gartners 2022 Top Security And Risk Management Trends Consolidating
Gartners 2022 Top Security And Risk Management Trends Consolidating
2481×3864
What Is A Computer Security Risk Definition And Types Lesson
What Is A Computer Security Risk Definition And Types Lesson
800×500
Unlocking The Power Of Cyber Security Risk Management Are You Doing It
Unlocking The Power Of Cyber Security Risk Management Are You Doing It
1200×628
Security Risk Assessment What Is It And How Does It Work Sabtrax
Security Risk Assessment What Is It And How Does It Work Sabtrax
1600×1014
Spartantec Inc Wilmington All About Security Risk Assessment
Spartantec Inc Wilmington All About Security Risk Assessment
1920×1080
Smart Homes At Greater Security Risk Than Ever Techradar
Smart Homes At Greater Security Risk Than Ever Techradar
1645×1057
5 Essential Data Security Best Practices For Keeping Your Data Safe
5 Essential Data Security Best Practices For Keeping Your Data Safe
1200×801
Cisas Security By Design Initiative Is At Risk Heres A Path Forward
Cisas Security By Design Initiative Is At Risk Heres A Path Forward
1024×780
6 Common Saas Security Risks You Must Know In 2023 Cloudeagle
6 Common Saas Security Risks You Must Know In 2023 Cloudeagle
2560×1440
Security Risk Red Rubber Stamp Over A White Background Stock Photo Alamy
Security Risk Red Rubber Stamp Over A White Background Stock Photo Alamy
1650×1100
Security Risk Response Options Halkyn Security Blog
Security Risk Response Options Halkyn Security Blog
1024×1024
Understanding Security Risks In Defi 101 Blockchains
Understanding Security Risks In Defi 101 Blockchains
777×501
Cyber Security Threats And Attacks Aiesec Help Center
Cyber Security Threats And Attacks Aiesec Help Center
1024×802
Protective Security Threat Types Core Integrity
Protective Security Threat Types Core Integrity
1024×576
Ppt How To Mitigate The Cyber Security Risk Posed Powerpoint
Ppt How To Mitigate The Cyber Security Risk Posed Powerpoint
735×852
Sources Of Security Risks And Threats You Can Find This And More
Sources Of Security Risks And Threats You Can Find This And More
1024×1024
A Risk Managers Approach To Cyber Security Compass Cyber Security
A Risk Managers Approach To Cyber Security Compass Cyber Security
1024×768
Five Risk Control Strategies Security Risk Solutions Singapore
Five Risk Control Strategies Security Risk Solutions Singapore
600×525
Infographic Top 10 Cybersecurity Threats Of The Future Healthcare It
Infographic Top 10 Cybersecurity Threats Of The Future Healthcare It
