Formalized Insider Threat Program Part 2 Of 20 Cert Best Practices To
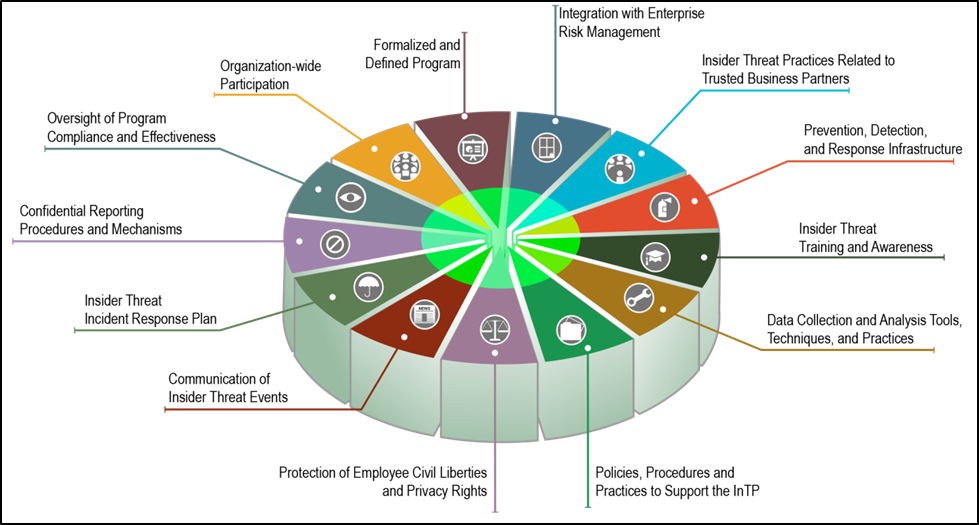
Find inspiration for Formalized Insider Threat Program Part 2 Of 20 Cert Best Practices To with our image finder website, Formalized Insider Threat Program Part 2 Of 20 Cert Best Practices To is one of the most popular images and photo galleries in Best Practices And Controls For Mitigating Insider Threats George Silowash Gallery, Formalized Insider Threat Program Part 2 Of 20 Cert Best Practices To Picture are available in collection of high-quality images and discover endless ideas for your living spaces, You will be able to watch high quality photo galleries Formalized Insider Threat Program Part 2 Of 20 Cert Best Practices To.
aiartphotoz.com is free images/photos finder and fully automatic search engine, No Images files are hosted on our server, All links and images displayed on our site are automatically indexed by our crawlers, We only help to make it easier for visitors to find a free wallpaper, background Photos, Design Collection, Home Decor and Interior Design photos in some search engines. aiartphotoz.com is not responsible for third party website content. If this picture is your intelectual property (copyright infringement) or child pornography / immature images, please send email to aiophotoz[at]gmail.com for abuse. We will follow up your report/abuse within 24 hours.
Related Images of Formalized Insider Threat Program Part 2 Of 20 Cert Best Practices To
Best Practices And Controls For Mitigating Insider Threats George Silowash
Best Practices And Controls For Mitigating Insider Threats George Silowash
768×593
Insider Threats Security Controls And Best Practices Exodesk
Insider Threats Security Controls And Best Practices Exodesk
1024×536
2021 Forrester Report On Best Practices Mitigating Insider Threats
2021 Forrester Report On Best Practices Mitigating Insider Threats
500×773
Mitigating Insider Threats Plan Your Actions In Advance Ekran System
Mitigating Insider Threats Plan Your Actions In Advance Ekran System
825×345
Pdf Best Practices For Mitigating And Investigating €” Best
Pdf Best Practices For Mitigating And Investigating €” Best
813×1053
Pdf Mitigating Insider Threats In Cloud Environments Best Practices
Pdf Mitigating Insider Threats In Cloud Environments Best Practices
850×1100
Common Sense Guide To Mitigating Insider Threats Download Free Pdf
Common Sense Guide To Mitigating Insider Threats Download Free Pdf
768×1024
Insider Threats Best Practices For Detecting And Preventing An Attack
Insider Threats Best Practices For Detecting And Preventing An Attack
640×360
How Your Business Can Detect And Manage Insider Threats
How Your Business Can Detect And Manage Insider Threats
1080×1080
Mitigating Insider Threats Plan Your Actions In Advance Ekran System
Mitigating Insider Threats Plan Your Actions In Advance Ekran System
825×600
2021 Forrester Report On Best Practices Mitigating Insider Threats
2021 Forrester Report On Best Practices Mitigating Insider Threats
500×647
New Research And Best Practices For Mitigating Insider Threats Global
New Research And Best Practices For Mitigating Insider Threats Global
515×287
A Strategic Approach To Mitigating Insider Threats
A Strategic Approach To Mitigating Insider Threats
1024×1024
Best Practices To Prevent Insider Threats Fileproinfo Blogs
Best Practices To Prevent Insider Threats Fileproinfo Blogs
1200×675
Understanding And Mitigating Insider Cybersecurity Threats Morefield
Understanding And Mitigating Insider Cybersecurity Threats Morefield
960×480
Common Sense Guide To Mitigating Insider Threats Pdf
Common Sense Guide To Mitigating Insider Threats Pdf
495×640
Insider Threat Prevention Best Practices Nordlayer
Insider Threat Prevention Best Practices Nordlayer
1280×635
Best Practices For Mitigating Insider Threats Veriato
Best Practices For Mitigating Insider Threats Veriato
1000×676
Insider Threats Protecting Your Organization From Within Synoptek
Insider Threats Protecting Your Organization From Within Synoptek
930×500
Best Practices Mitigating Insider Threats And Misuse Of Data
Best Practices Mitigating Insider Threats And Misuse Of Data
1200×675
10 Best Practices For Mitigating Insider Threat Risks In A Hybrid
10 Best Practices For Mitigating Insider Threat Risks In A Hybrid
1024×683
The 13 Key Elements Of An Insider Threat Program
The 13 Key Elements Of An Insider Threat Program
1238×720
Best Practicesmitigating Insider Threats Cyentia Cybersecurity
Best Practicesmitigating Insider Threats Cyentia Cybersecurity
495×640
The Key To Mitigating Insider Security Threats Kovair Blog
The Key To Mitigating Insider Security Threats Kovair Blog
1000×500
Your Security Guide To Insider Threat Protection 10 Best Practices To
Your Security Guide To Insider Threat Protection 10 Best Practices To
825×502
Understanding And Managing Insider Threats In Cybersecurity Reveal
Understanding And Managing Insider Threats In Cybersecurity Reveal
500×500
What Are Insider Threats 2024 Cyber Security Guide
What Are Insider Threats 2024 Cyber Security Guide
750×435
Mitigating Insider Threats In The Telecommunications Industry
Mitigating Insider Threats In The Telecommunications Industry
1200×628
Best Practices For Implementing An Insider Threat Program
Best Practices For Implementing An Insider Threat Program
640×360
Mitigating The Insider Threat Step 1 User Privilege Performance
Mitigating The Insider Threat Step 1 User Privilege Performance
2155×1124
How To Mitigate Insider Threats By Learning From Past Incidents
How To Mitigate Insider Threats By Learning From Past Incidents
624×360
6 Types Of Insider Threats And How To Prevent Them Techtarget
6 Types Of Insider Threats And How To Prevent Them Techtarget
558×362
Formalized Insider Threat Program Part 2 Of 20 Cert Best Practices To
Formalized Insider Threat Program Part 2 Of 20 Cert Best Practices To
979×525
