Practical Use Of Cryptography Instant Messaging Application
Find inspiration for Practical Use Of Cryptography Instant Messaging Application with our image finder website, Practical Use Of Cryptography Instant Messaging Application is one of the most popular images and photo galleries in Practical Use Of Cryptography Instant Messaging Application Gallery, Practical Use Of Cryptography Instant Messaging Application Picture are available in collection of high-quality images and discover endless ideas for your living spaces, You will be able to watch high quality photo galleries Practical Use Of Cryptography Instant Messaging Application.
aiartphotoz.com is free images/photos finder and fully automatic search engine, No Images files are hosted on our server, All links and images displayed on our site are automatically indexed by our crawlers, We only help to make it easier for visitors to find a free wallpaper, background Photos, Design Collection, Home Decor and Interior Design photos in some search engines. aiartphotoz.com is not responsible for third party website content. If this picture is your intelectual property (copyright infringement) or child pornography / immature images, please send email to aiophotoz[at]gmail.com for abuse. We will follow up your report/abuse within 24 hours.
Related Images of Practical Use Of Cryptography Instant Messaging Application
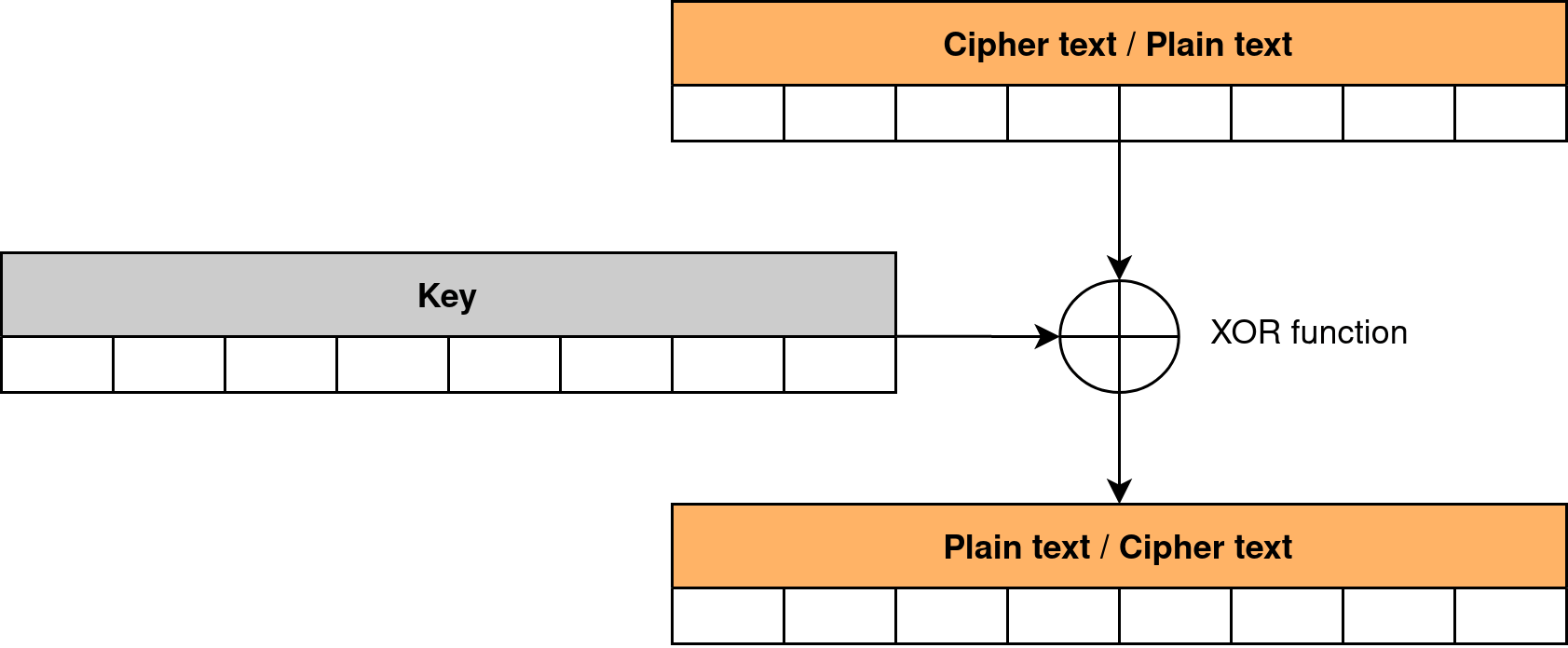
Practical Use Of Cryptography Instant Messaging Application
Practical Use Of Cryptography Instant Messaging Application
984×912
Practical Use Of Cryptography Instant Messaging Application
Practical Use Of Cryptography Instant Messaging Application
844×1024
Practical Use Of Cryptography Instant Messaging Application
Practical Use Of Cryptography Instant Messaging Application
1536×1266
Practical Use Of Cryptography Instant Messaging Application
Practical Use Of Cryptography Instant Messaging Application
891×932
Practical Use Of Cryptography Instant Messaging Application
Practical Use Of Cryptography Instant Messaging Application
1746×966
Practical Use Of Cryptography Instant Messaging Application
Practical Use Of Cryptography Instant Messaging Application
678×499
Practical Use Of Cryptography Instant Messaging Application
Practical Use Of Cryptography Instant Messaging Application
2048×826
Practical Use Of Cryptography Instant Messaging Application
Practical Use Of Cryptography Instant Messaging Application
1536×1113
Practical Use Of Cryptography Instant Messaging Application
Practical Use Of Cryptography Instant Messaging Application
1024×893
Practical Use Of Cryptography Instant Messaging Application
Practical Use Of Cryptography Instant Messaging Application
3036×1233
Practical Use Of Cryptography Instant Messaging Application
Practical Use Of Cryptography Instant Messaging Application
850×416
Pdf End To End Encryption On The Instant Messaging Application Based
Pdf End To End Encryption On The Instant Messaging Application Based
850×1203
Cryptography Demystified Protecting Your Digital Privacy
Cryptography Demystified Protecting Your Digital Privacy
894×451
Figure 2 From Design And Implementation Of A Secure Instant Messaging
Figure 2 From Design And Implementation Of A Secure Instant Messaging
672×444
How To Make A Really Secure Messaging App Like Signal Mind Studios
How To Make A Really Secure Messaging App Like Signal Mind Studios
1440×1085
Github Darshasawacryptography Implementing Various Cipher
Github Darshasawacryptography Implementing Various Cipher
2048×938
加密初学者指南。 Beginners Guide To Cryptography Quick博客
加密初学者指南。 Beginners Guide To Cryptography Quick博客
1001×553
Role Of Cryptography In Information Security Cloudkul
Role Of Cryptography In Information Security Cloudkul
914×522
Types Of Cryptography A Comprehensive Guide Core Devs Ltd
Types Of Cryptography A Comprehensive Guide Core Devs Ltd
1024×768
Cryptographic Keys 101 What They Are And How They Secure Data Hashed
Cryptographic Keys 101 What They Are And How They Secure Data Hashed
942×547
An Introduction To Post Quantum Cryptography Crypto Quantique
An Introduction To Post Quantum Cryptography Crypto Quantique
1600×900
Ultimate Guide To Understanding What Symmetric Key Cryptography Is 2023
Ultimate Guide To Understanding What Symmetric Key Cryptography Is 2023
1536×856
Figure 1 From Design And Implementation Of A Secure Instant Messaging
Figure 1 From Design And Implementation Of A Secure Instant Messaging
1028×236
Cryptography Different Types Tools And Its Applications
Cryptography Different Types Tools And Its Applications
881×485
Pdf Development Of Cryptography Based Secure Messaging System
Pdf Development Of Cryptography Based Secure Messaging System
524×524
Blockchain Cryptography And Digital Signatures Toughnickel
Blockchain Cryptography And Digital Signatures Toughnickel
1200×863
Blockchain Cryptography Everything You Need To Know 101 Blockchains
Blockchain Cryptography Everything You Need To Know 101 Blockchains
1024×384
Sample Application Of The Three Cryptographic Techniques Download
Sample Application Of The Three Cryptographic Techniques Download
850×497
The Best Encrypted Messaging Apps You Should Use Today Updated 2019
The Best Encrypted Messaging Apps You Should Use Today Updated 2019
1200×1500
10 Best Encrypted Messaging Apps For Secure Business Communication In 2023
10 Best Encrypted Messaging Apps For Secure Business Communication In 2023
1500×1280
