What Is A Cybersecurity Strategy And How Can Your Business Develop One
Find inspiration for What Is A Cybersecurity Strategy And How Can Your Business Develop One with our image finder website, What Is A Cybersecurity Strategy And How Can Your Business Develop One is one of the most popular images and photo galleries in Building A Robust Cybersecurity Strategy A Look At Frameworks And Best Gallery, What Is A Cybersecurity Strategy And How Can Your Business Develop One Picture are available in collection of high-quality images and discover endless ideas for your living spaces, You will be able to watch high quality photo galleries What Is A Cybersecurity Strategy And How Can Your Business Develop One.
aiartphotoz.com is free images/photos finder and fully automatic search engine, No Images files are hosted on our server, All links and images displayed on our site are automatically indexed by our crawlers, We only help to make it easier for visitors to find a free wallpaper, background Photos, Design Collection, Home Decor and Interior Design photos in some search engines. aiartphotoz.com is not responsible for third party website content. If this picture is your intelectual property (copyright infringement) or child pornography / immature images, please send email to aiophotoz[at]gmail.com for abuse. We will follow up your report/abuse within 24 hours.
Related Images of What Is A Cybersecurity Strategy And How Can Your Business Develop One
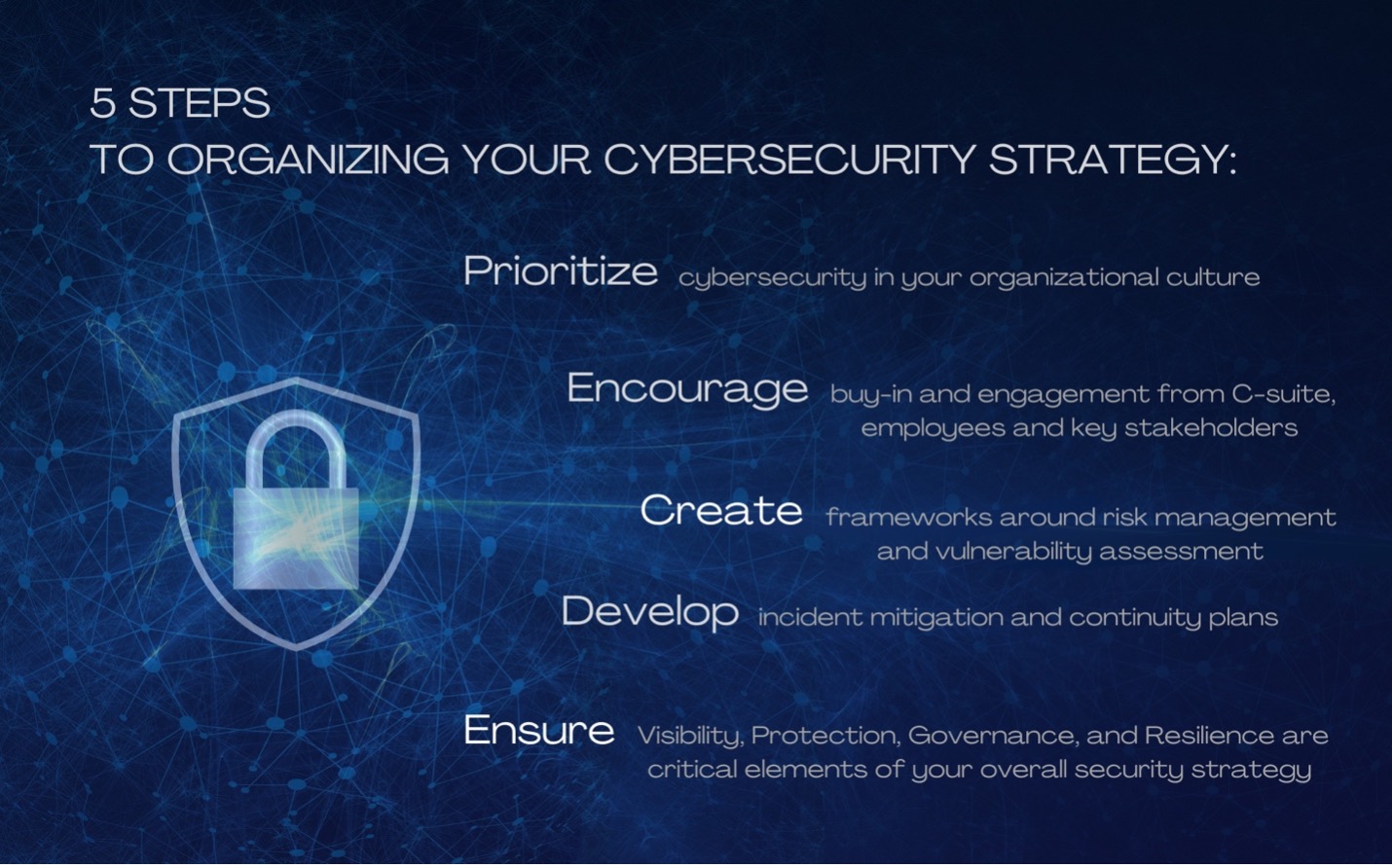
Building A Robust Cybersecurity Strategy A Look At Frameworks And Best
Building A Robust Cybersecurity Strategy A Look At Frameworks And Best
1280×720
How To Develop A Cybersecurity Strategy Step By Step Guide Techtarget
How To Develop A Cybersecurity Strategy Step By Step Guide Techtarget
560×351
Cs5l Cmm Cybersecurity Strategy 5 Layout Capability Maturity Model
Cs5l Cmm Cybersecurity Strategy 5 Layout Capability Maturity Model
1568×1600
Understanding Cybersecurity Frameworks A Beginners Guide Clarusway
Understanding Cybersecurity Frameworks A Beginners Guide Clarusway
1387×692
Cybersecurity Strategy Seven Steps To Develop A Strong Plan
Cybersecurity Strategy Seven Steps To Develop A Strong Plan
675×450
7 Common Cybersecurity Frameworks To Reduce Cyber Risk Netraclos Inc
7 Common Cybersecurity Frameworks To Reduce Cyber Risk Netraclos Inc
1024×683
Tips For Building A Robust Cybersecurity Strategy
Tips For Building A Robust Cybersecurity Strategy
1200×628
How To Create A Robust Cyber Security Strategy Dincloud
How To Create A Robust Cyber Security Strategy Dincloud
768×393
7 Building Blocks Of An Effective Cyber Security Strategy Spectral
7 Building Blocks Of An Effective Cyber Security Strategy Spectral
1024×1024
How To Build A Robust Cybersecurity Strategy For Your Startup
How To Build A Robust Cybersecurity Strategy For Your Startup
900×630
Cybersecurity Strategy Seven Steps To Develop A Strong Plan
Cybersecurity Strategy Seven Steps To Develop A Strong Plan
3750×1963
How It Security Frameworks Can Help Reduce Cybersecurity Risk
How It Security Frameworks Can Help Reduce Cybersecurity Risk
634×459
What Is A Cybersecurity Strategy And How Can Your Business Develop One
What Is A Cybersecurity Strategy And How Can Your Business Develop One
1430×892
How To Build A Cybersecurity Strategy A Comprehensive Guide Cyber
How To Build A Cybersecurity Strategy A Comprehensive Guide Cyber
1068×552
Best Cybersecurity Frameworks Nist Iso27001 And Other Standards
Best Cybersecurity Frameworks Nist Iso27001 And Other Standards
500×300
10 Cybersecurity Frameworks You Need To Know About Help Net Security
10 Cybersecurity Frameworks You Need To Know About Help Net Security
1456×816
How To Implement A Robust Cybersecurity Program
How To Implement A Robust Cybersecurity Program
600×400
Exploring Top 6 Cybersecurity Frameworks For Businesses A Complete
Exploring Top 6 Cybersecurity Frameworks For Businesses A Complete
750×500
What Are Cybersecurity Frameworks And Their Types Techno Digits
What Are Cybersecurity Frameworks And Their Types Techno Digits
1200×630
How To Choose A Cybersecurity Framework For Your Business Vertikal6
How To Choose A Cybersecurity Framework For Your Business Vertikal6
1200×709
Cybersecurity Frameworks Standards And Best Practices
Cybersecurity Frameworks Standards And Best Practices
1064×720
Long Term Cybersecurity Strategy Building A Robust Approach
Long Term Cybersecurity Strategy Building A Robust Approach
750×440
Cybersecurity Strategy What Are The Key Aspects To Consider
Cybersecurity Strategy What Are The Key Aspects To Consider
699×400
Wazuh Building Robust Cybersecurity Architecture With Open Source
Wazuh Building Robust Cybersecurity Architecture With Open Source
1601×901
Mastering The Top Cybersecurity Frameworks To Defend Your Digital
Mastering The Top Cybersecurity Frameworks To Defend Your Digital
1200×616
Developing A Robust Cybersecurity Training Strategy
Developing A Robust Cybersecurity Training Strategy
640×366
The Ultimate Guide To Building An Effective Cybersecurity Strategy
The Ultimate Guide To Building An Effective Cybersecurity Strategy
870×272
Cybersecurity Threats Mitigation Step By Step Plan
Cybersecurity Threats Mitigation Step By Step Plan
960×720
Cybersecurity Threats And Attacks All You Need To Know
Cybersecurity Threats And Attacks All You Need To Know
700×482
Cybersecurity Frameworks — Types Strategies Implementation And Benefits
Cybersecurity Frameworks — Types Strategies Implementation And Benefits
728×380
Understanding The 3 Phases Of Cybersecurity Architecture Ardoq
Understanding The 3 Phases Of Cybersecurity Architecture Ardoq
3000×1500
Introduction To The Nist Cybersecurity Framework For A Landscape Of
Introduction To The Nist Cybersecurity Framework For A Landscape Of
695×437
Most Common Cybersecurity Frameworks And Types E Spin Group
Most Common Cybersecurity Frameworks And Types E Spin Group
1024×576
