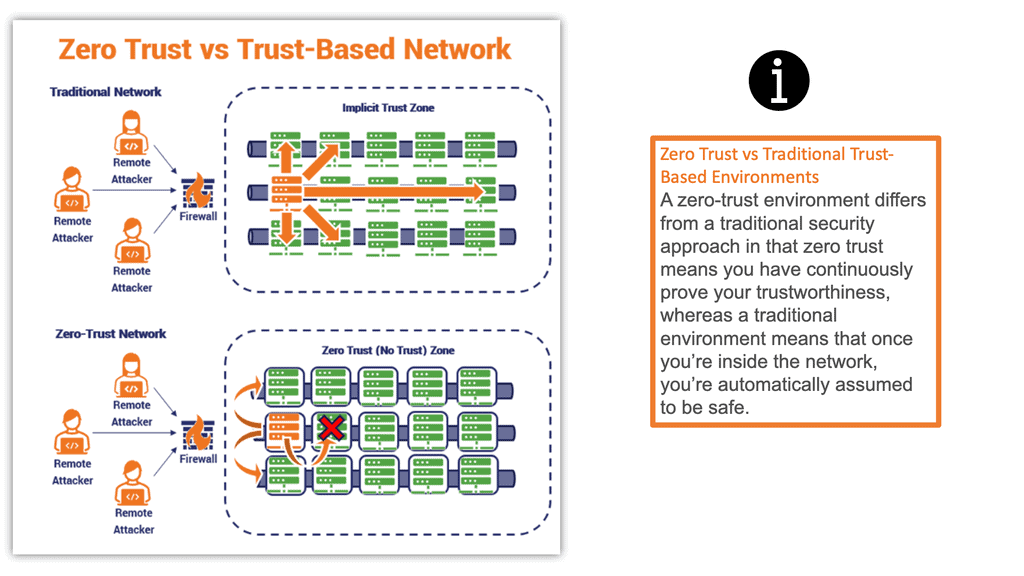
Zero Trust Network Design
Find inspiration for Zero Trust Network Design with our image finder website, Zero Trust Network Design is one of the most popular images and photo galleries in Zero Trust Network Design Gallery, Zero Trust Network Design Picture are available in collection of high-quality images and discover endless ideas for your living spaces, You will be able to watch high quality photo galleries Zero Trust Network Design.
aiartphotoz.com is free images/photos finder and fully automatic search engine, No Images files are hosted on our server, All links and images displayed on our site are automatically indexed by our crawlers, We only help to make it easier for visitors to find a free wallpaper, background Photos, Design Collection, Home Decor and Interior Design photos in some search engines. aiartphotoz.com is not responsible for third party website content. If this picture is your intelectual property (copyright infringement) or child pornography / immature images, please send email to aiophotoz[at]gmail.com for abuse. We will follow up your report/abuse within 24 hours.
Related Images of Zero Trust Network Design
Zero Trust Networks What They Are And How To Implement One Onx
Zero Trust Networks What They Are And How To Implement One Onx
1024×569
Solutions Zero Trust Frameworks Architecture Guide Cisco
Solutions Zero Trust Frameworks Architecture Guide Cisco
2070×892
Building A Zero Trust Visibility Architecture
Building A Zero Trust Visibility Architecture
2000×1196
Embracing A Zero Trust Security Model Logrhythm
Embracing A Zero Trust Security Model Logrhythm
1024×1024
The Comprehensive Guide To Zero Trust Architecture
The Comprehensive Guide To Zero Trust Architecture
1259×1080
Rh Isac Zero Trust Architecture Zta How To Get Started
Rh Isac Zero Trust Architecture Zta How To Get Started
1200×1200
Zero Trust Network Design Principles And Considerations
Zero Trust Network Design Principles And Considerations
680×450
Zero Trust Model Architecture And Implementation Cybersecurity Memo
Zero Trust Model Architecture And Implementation Cybersecurity Memo
1600×939
What Is Zero Trust Network Access Ztna The Zero Trust Model
What Is Zero Trust Network Access Ztna The Zero Trust Model
2560×1978
Is Zero Trust Architecture The Method Of Future Cybersecurity
Is Zero Trust Architecture The Method Of Future Cybersecurity
1440×1109
Zero Trust Network Access Ztna A Complete Guide
Zero Trust Network Access Ztna A Complete Guide
950×534
How To Build A Zero Trust Network In 4 Steps Techtarget
How To Build A Zero Trust Network In 4 Steps Techtarget
1658×747
5 Principles To Achieve Zero Trust For The Workforce Establish User
5 Principles To Achieve Zero Trust For The Workforce Establish User
1174×661
Implementing A Zero Trust Security Model At Microsoft
Implementing A Zero Trust Security Model At Microsoft
1200×675
The Zero Trust Approach To Important Control Planes Duo Security
The Zero Trust Approach To Important Control Planes Duo Security
1024×576
Implementing A Zero Trust Security Model At Microsoft
Implementing A Zero Trust Security Model At Microsoft
1280×720
Zero Trust Model Endpoint Initiated Zero Trust Network Topology Model
Zero Trust Model Endpoint Initiated Zero Trust Network Topology Model
662×349
The 5 Steps To Building A Zero Trust Network Secureops
The 5 Steps To Building A Zero Trust Network Secureops
